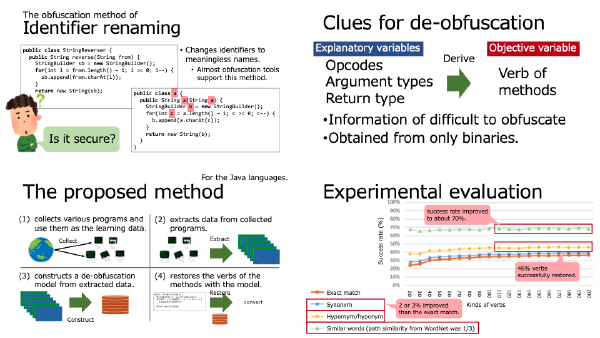
:speaking_head: Overview # The obfuscation methods are often used to hide sensitive information in software. Especially, an identifier renaming method (IRM) is well used because it is easy to implement. IRM is one of the obfuscation methods, and to change the names of function, and variables into meaningless one. However, if we can restore the identifiers to the original names, IRM is invalidated. One of the serious problems about IRM is that the tolerance against de-obfuscation is not discussed. This paper tries to de-obfuscate IRMed programs. Thereby, this paper evaluates the tolerance and effectiveness of IRM. From the experimental evaluation, the proposed method can restore the 49.71 % of method names to the original verbs. Furthermore, focusing on the meanings of verbs, the proposed method recommends the verbs of similar meanings to the original verbs in 57.01 % of methods.
:speaking_head: Overview # It is crucial for educators to understand pitfalls for novice programmers in programming education at computer science course. By giving well-timed advice to students who fall into a pitfall, educators are able to achieve efficient teaching and keep up their students’ motivation. However, so far, it is less well-understood how novice students edit source code and why they fall into a pitfall. In this paper, we analyzed coding patterns of novice students empirically. We collected programming activities by students on exercises of programming course, and then performed qualitative and quantitative analysis. In qualitative analysis, experienced programmers analyzed patterns of the novice programmers manually. In quantitative analysis, we focused on transtions of the edit distance between a source code of each student under development and a correct source code in a programming class. As a result, we confirmed coding patterns of novice programmers in case of falling into pitfalls, and the characteristics of transitions of edit distance metric in the case that novice students had faced difficulty in understanding the exercise.
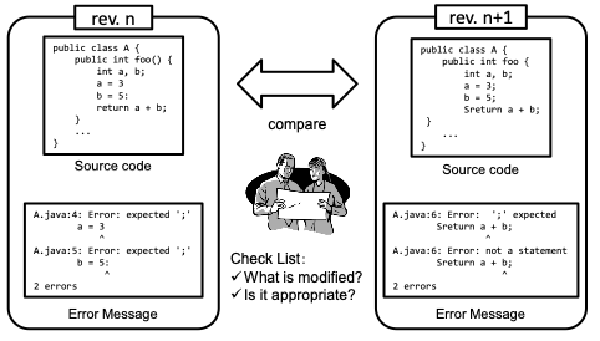
:speaking_head: Overview # This topic is for mining software repositories. The following surveys were done.
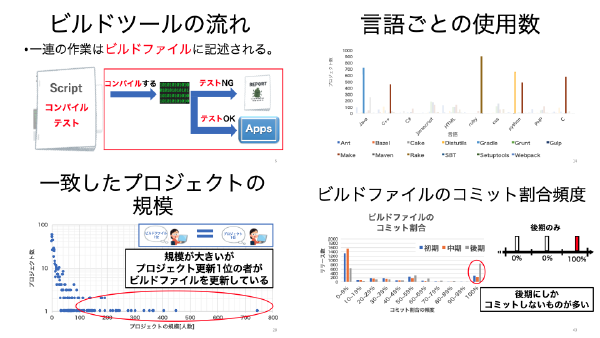
why do the developers update the build files in the project, and how to build the obliging bots for supporting next action. :books: Publications # 鐘ヶ江 由佳,玉田 春昭,畑 秀明,”GitHubにおける言語ごとのビルドファイルの更新理由調査”, 研究報告ソフトウェア工学(SE), Vol. 2017-SE-196, No.28, July 2017. Akira Inokuchi, Haruaki Tamada, Hideaki Hata, and Masateru Tsunoda, “Toward Obliging Bots for Supporting Next Actions,” In Proc. of the 4th International Conference on Applied Computing & Information Technology (ACIT 2016), pp. 183–188, December 2016 (UNLV, Las Vegas, NV, USA). :mag_right: Related Research Topics # Project as a City Characteristics of the developers :handshake: Collaborators # H. Hata@NAIST SE Lab. M. Tsunoda@Kindai University.
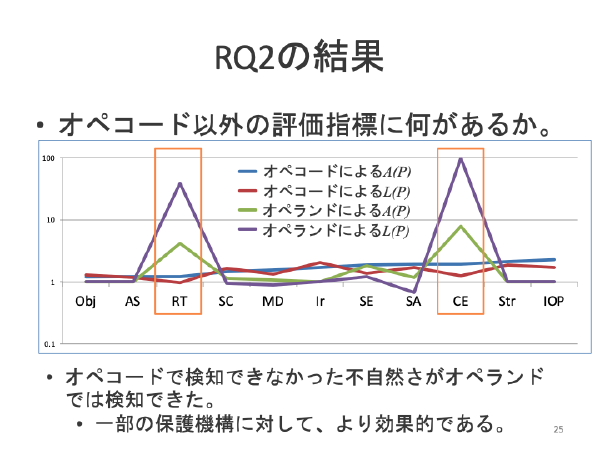
:speaking_head: Overview # This research topic tries to evaluate the artificialities of the obfuscated programs. We believe that the obfuscation changes the programs into unordinal ones. This topics evaluates the artificialities by tf-idf and perplexities.
:books: Publications # 横井 昂典,玉田 春昭,”使用クラスに基づいたTF-IDFによる難読化の不自然さ評価”,2017年暗号と情報セキュリティシンポジウム予稿集 (SCIS 2017),3D1-4,January 2017.(沖縄,那覇) 大滝 隆貴,大堂 哲也,玉田 春昭,神崎 雄一郎,門田 暁人,”Javaバイトコード命令のオペコード、オペランドを用いた難読化手法のステルシネス評価”,2014年暗号と情報セキュリティシンポジウム予稿集 (SCIS2014), 2D2-2, January 2014. :mag_right: Related Research Topics # Identifying the applied obfuscator De-obfuscate IRM (identifier renaming method) Evaluating obfuscation method by Kolmogorov complexity Unreadability evaluation of obfuscated programs :handshake: Collaborators # Y. Kanzaki@Kumamoto National College of Technology
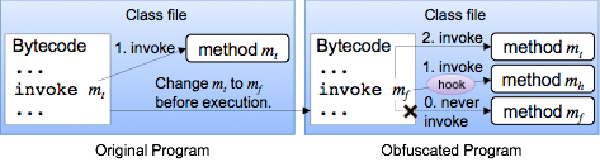
:speaking_head: Overview # This paper proposes an obfuscation method against illegal analysis. The proposed method tries to build a fake call flow graph from debugging tools. The call flow graph represents relations among methods and helps understanding of a program. The fake call flow graph leads misunderstanding of the program. We focus on a hook mechanism of the method call for changing a callee. We conduct two experiments to evaluate the proposed method. First experiment simulates attacks by existing tools: Soot, jad, Procyon, and Krakatau. The Procyon only succeeded decompilation, the others crashed. Second experiment evaluates understandability of the obfuscated program by the hand. Only one subject in the nine subjects answered the correct value. The experiments shows the proposed method has good tolerance against existing tools, and high difficulty of understanding even if the target program is tiny and simple program. (Abstract from IJSI 2015)
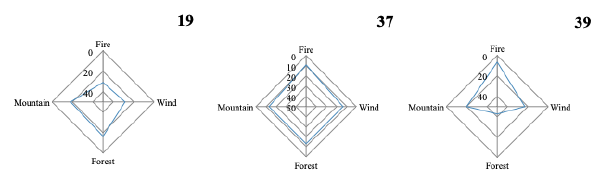
:speaking_head: Overview # In software development, multiple developers compose a team, and perform a development process. To succeed the development, understanding developers’ characteristics are needed. However, there is no way to measure the characteristics of the developer by quantitative analysis. Therefore, a project manager often assigns team members based on his/her own sense, considering experience year of them.