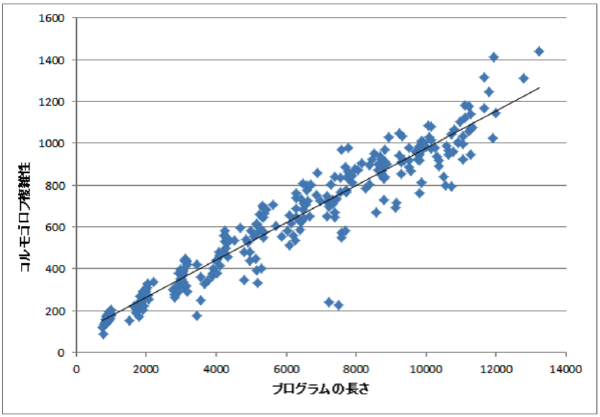
:speaking_head: Overview # This paper quantifies the diffuculty of program analysis based on the information theory. The basic idea is to consider that a program ultimately obscated if instructions appear at random; that is (1) all instructions has an equal frequency of appearance, and (2) there is no pattern observed in the instruction sequence. We quantified (1) based on the entropy and (2) based on the Kolmogorov complexity. We evaluated the feasibility of our proposal through a case study.
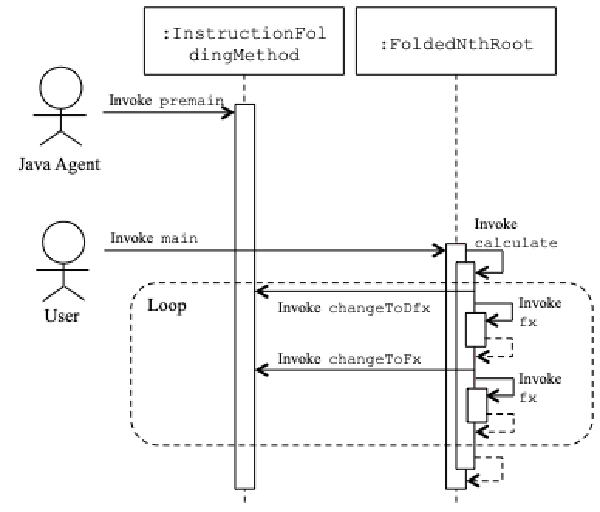
:speaking_head: Overview # To improve tamper resistance of programs against illegal modification, this paper proposes instruction folding applicable to Java platform.
In the proposed method, at first, similar methods are selected in a Java program. Next, these methods are merged into one method and diffs among these methods are stored in the program. Then, at runtime, when one of the merged methods is executed, diffs are restored by self-modification, which is realized by the Java instrumentation mechanism. The proposed method is resilient against tampering of folded method. Even if an adversary modifies the folded method, the program goes crash because the method is repeatedly modified at runtime.
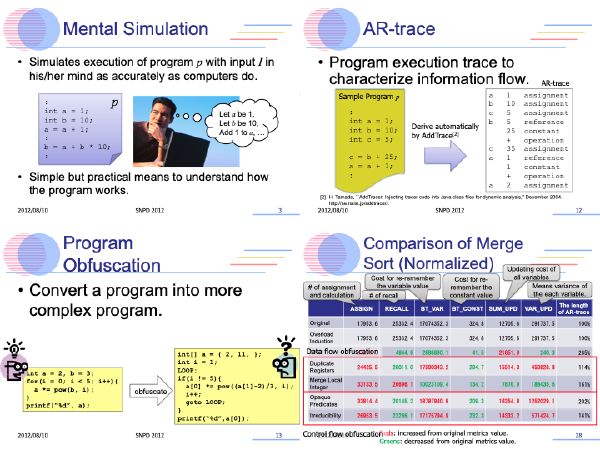
:speaking_head: Overview # Obfuscation methods were proposed for protecting programs from cracking. These methods convert program into incomprehensible one, such as change symbol names from meaningful to meaningless. As a result, secret information in the program can be hidden. However, obfuscation methods are not evaluated sufficiently. This paper evaluates incomprehensibility of the obfuscated programs using queue based virtual mental simulation model (VMSM) which is focused on short term memory in program comprehension. An experimental evaluation showed that VMSM was able to evaluate the incomprehensibility of data and control flow obfuscation methods.
:speaking_head: Overview # This research topics shows applications of software birthmarks. In our publications, we try to classify the programs using extracted software birthmarks. Because, we believe that the birthmarks shows the functionalities of the programs.
:books: Publications # 牛窓 朋義, 門田 暁人, 玉田 春昭, 松本 健一, “使用クラスに基づくソフトウェアの機能面からの分類”, 信学技報 ソフトウェアサイエンス研究会, Vol.SS2009-17, pp.31-36, August 2009. 玉田 春昭,森崎 修司,門田 暁人,松本 健一,”バースマークを用いたソフトウェア拡張開発での流用度合いの測定”,情報処理学会第70回全国大会,pp.5-399-400, March 2008. Takesi Kakimoto, Akito Monden, Yasutaka Kamei, Haruaki Tamada, Masateru Tsunoda, and Ken-ichi Matsumoto, “Using Software Birthmarks to Identify Similar Classes and Major Functionalities,” In Proc. the 3rd International Workshop on Mining Software Repositories (MSR 2006), pp.171-172, May 2006. (Shanghai, China) Link dl.acm.org :mag_right: Related Research Topics # Concept of Software Birthmarks Dynamic Software Birthmarks Fast comparisons of the birthmarks :handshake: Collaborators # A. Monden@Software mesurement and analytics laboratory, Okayama University
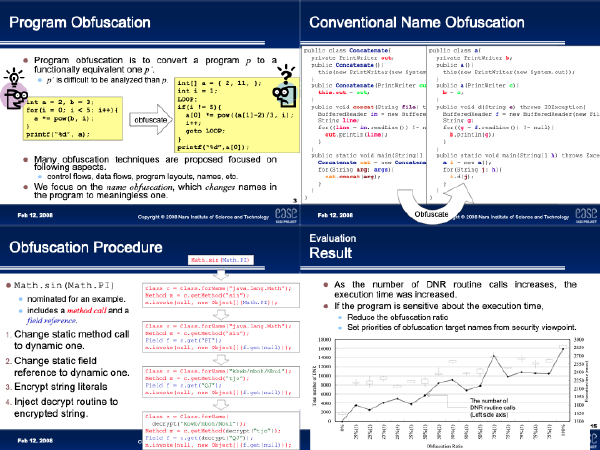
:speaking_head: Overview # Name obfuscation is a software protection technique, which renames identifiers in a given program, to protect the program from illegal cracking. The conventional methods replace names appearing in the declaration part with the meaningless ones. Therefore, the methods cannot be used to obfuscate names declared in system libraries, since changing such system-defined names significantly deteriorates the program portability.
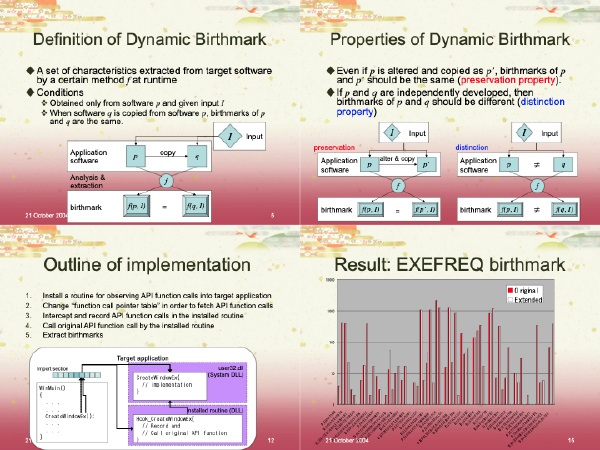
:speaking_head: Overview # This paper presents a technique of dynamic software birthmarks to support efficient detection of software theft. A dynamic birthmark $f(p, I)$ is a set of unique and native characteristics of a program $p$, obtained by executing $p$ with a given input $I$. For a pair of software $p$ and $q$, if $f(p, I) = f(q, I)$ holds, $q$ is suspected as a copy of $p$. In this paper, we propose two kinds of dynamic birthmarks, EXESEQ and EXEFREQ which use execution order and frequency distribution of runtime API Calls. In the first experiment, we applied the proposed birthmarks to the same-purpose applications. As a result, it was shown that an application and its extended version have quite similar birthmarks, and that the applications that are independently implemented possess significantly different birthmarks. The second experiment showed that the proposed birthmarks achieve the strong resilience against the usage of different compilers and optimizations.