Getting ways of the version defined in pom.xml Constant Property Package Module What the case in the use of native-image? Result of Measurements Summary References Getting ways of the version defined in pom.xml # Java 17が出たことだし,いい加減に Java のモジュールシステムを本格的に使いだそうとしている. 最近のJavaの自作ツールは一応モジュール対応にしたつもり(pochi,vhcなど).
で,ビルドツールは Maven を使うことが多いのだけど,pom.xml で設定したバージョン情報をアプリケーションからどんな情報で取得できるかを確認してみた.
次の4つの方法に分類できる.
Constant: 自分でバージョンの文字列をString型リテラルとしてソースコードに書き込む. Property: src/main/resourcesにプロパティファイルとしてバージョン情報を置いておく. Package: MANIFEST.MFに書かれている Implementation-VersionやSpecification-Versionのいずれかを利用する. Module: ModuleDescriptorのversionメソッドから利用する. それぞれの分類を独断と偏見で4段階で評価してみた(1が良くて,4が悪い).
Unit tests runner/coverage calculator on the CLI environment for the Java platform.
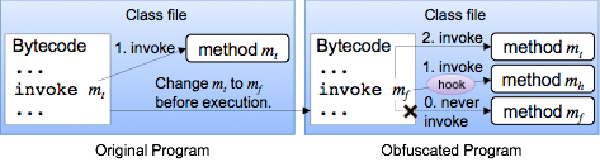
:speaking_head: Overview # This paper proposes an obfuscation method against illegal analysis. The proposed method tries to build a fake call flow graph from debugging tools. The call flow graph represents relations among methods and helps understanding of a program. The fake call flow graph leads misunderstanding of the program. We focus on a hook mechanism of the method call for changing a callee. We conduct two experiments to evaluate the proposed method. First experiment simulates attacks by existing tools: Soot, jad, Procyon, and Krakatau. The Procyon only succeeded decompilation, the others crashed. Second experiment evaluates understandability of the obfuscated program by the hand. Only one subject in the nine subjects answered the correct value. The experiments shows the proposed method has good tolerance against existing tools, and high difficulty of understanding even if the target program is tiny and simple program. (Abstract from IJSI 2015)
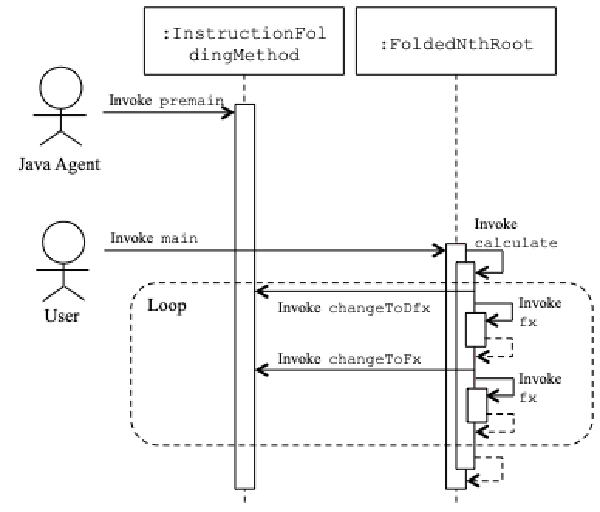
:speaking_head: Overview # To improve tamper resistance of programs against illegal modification, this paper proposes instruction folding applicable to Java platform.
In the proposed method, at first, similar methods are selected in a Java program. Next, these methods are merged into one method and diffs among these methods are stored in the program. Then, at runtime, when one of the merged methods is executed, diffs are restored by self-modification, which is realized by the Java instrumentation mechanism. The proposed method is resilient against tampering of folded method. Even if an adversary modifies the folded method, the program goes crash because the method is repeatedly modified at runtime.
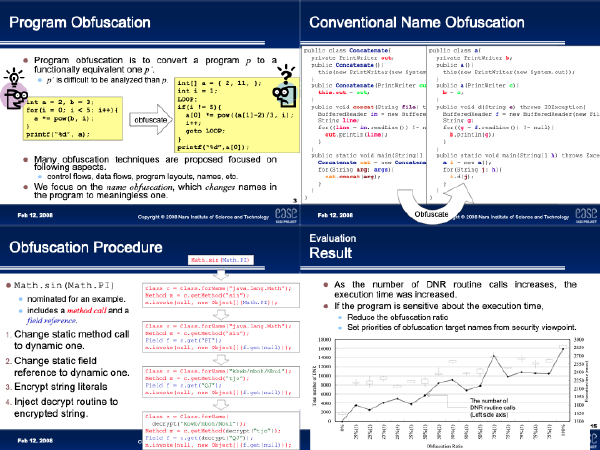
:speaking_head: Overview # Name obfuscation is a software protection technique, which renames identifiers in a given program, to protect the program from illegal cracking. The conventional methods replace names appearing in the declaration part with the meaningless ones. Therefore, the methods cannot be used to obfuscate names declared in system libraries, since changing such system-defined names significantly deteriorates the program portability.