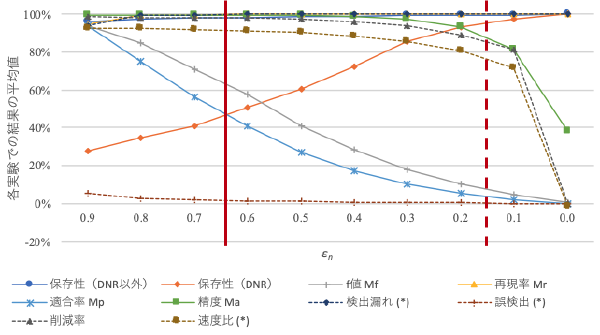
:speaking_head: Overview # The software birthmarks were proposed for detecting the software theft from a large number of suspected programs. The birthmark is a technique to compare the extracted characteristics as the software birthmarks, and compute similarities between two birthmarks. The conventional birthmarks require a much time by increasing the target programs for comparison. Therefore, it is the bottleneck of the conventional birthmarking technique. In this paper, we propose a method for reducing total processing time by introducing the narrowing phase between conventional extracting and comparison phases. The narrowing phase employs the fast but rough comparison algorithm in order to eliminate unrelated programs.
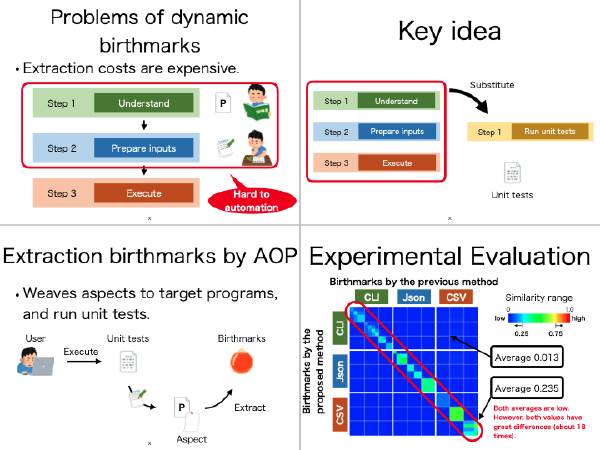
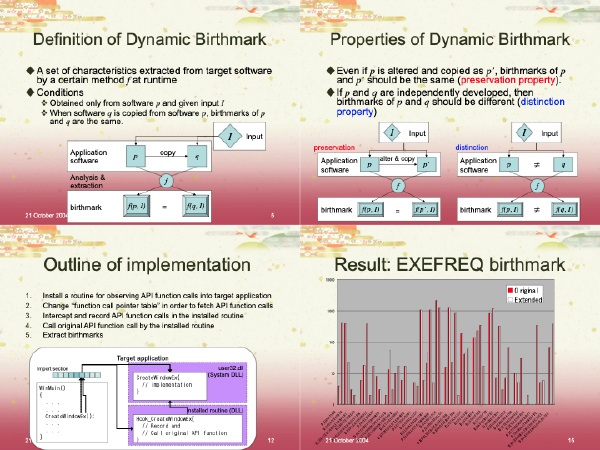
:speaking_head: Overview # The software birthmark methods are proposed to find the stolen software from the huge number of suspects. The software birthmark methods are classified into two manners, static and dynamic manners. Different from the static birthmarks, dynamic birthmarks require inputs since they base on runtime behaviors. Also, the dynamic birthmark varies depending on the inputs, therefore, it is difficult to extract beforehand. Hence the extraction cost of the dynamic birthmarks is generally high than the static birthmarks. This paper focuses on unit test codes in a project in order to extract the dynamic birthmarks beforehand, and reduce the extraction cost. The experiments evaluated the credibility and resilience performance of the birthmarks. The performance evaluation showed good results, the similarities were greater than 0.8 between most recent two versions of the same products, and were under 0.355 among different projects. In the cost evaluation, the proposed method can reduce the extraction cost of dynamic birthmarks.
:speaking_head: Overview # This paper presents a technique of dynamic software birthmarks to support efficient detection of software theft. A dynamic birthmark $f(p, I)$ is a set of unique and native characteristics of a program $p$, obtained by executing $p$ with a given input $I$. For a pair of software $p$ and $q$, if $f(p, I) = f(q, I)$ holds, $q$ is suspected as a copy of $p$. In this paper, we propose two kinds of dynamic birthmarks, EXESEQ and EXEFREQ which use execution order and frequency distribution of runtime API Calls. In the first experiment, we applied the proposed birthmarks to the same-purpose applications. As a result, it was shown that an application and its extended version have quite similar birthmarks, and that the applications that are independently implemented possess significantly different birthmarks. The second experiment showed that the proposed birthmarks achieve the strong resilience against the usage of different compilers and optimizations.
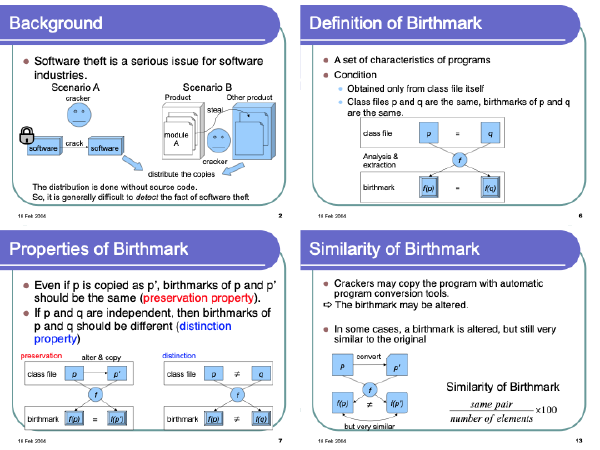
:speaking_head: Overview # To detect the theft of Java class files efficiently, we propose a concept of Java birthmarks, which are unique and native characteristics of every class file. For a pair of class files $p$ and $q$, if $q$ has the same birthmark as $p$’s, $q$ is suspected as a copy of $p$. Ideally, the birthmarks should satisfy the following properties: (a) preservation – the birthmarks should be preserved even if the original class file is tampered with, and (b) distinction – independent class files must be distinguished by completely different birthmarks. Taking (a) and (b) into account, we propose four types of birthmarks for Java class files.